Privileged Access Management
Secure your sensitive data with ease - PAM solutions offer complete control over access permissions, protecting your business from potential threats.
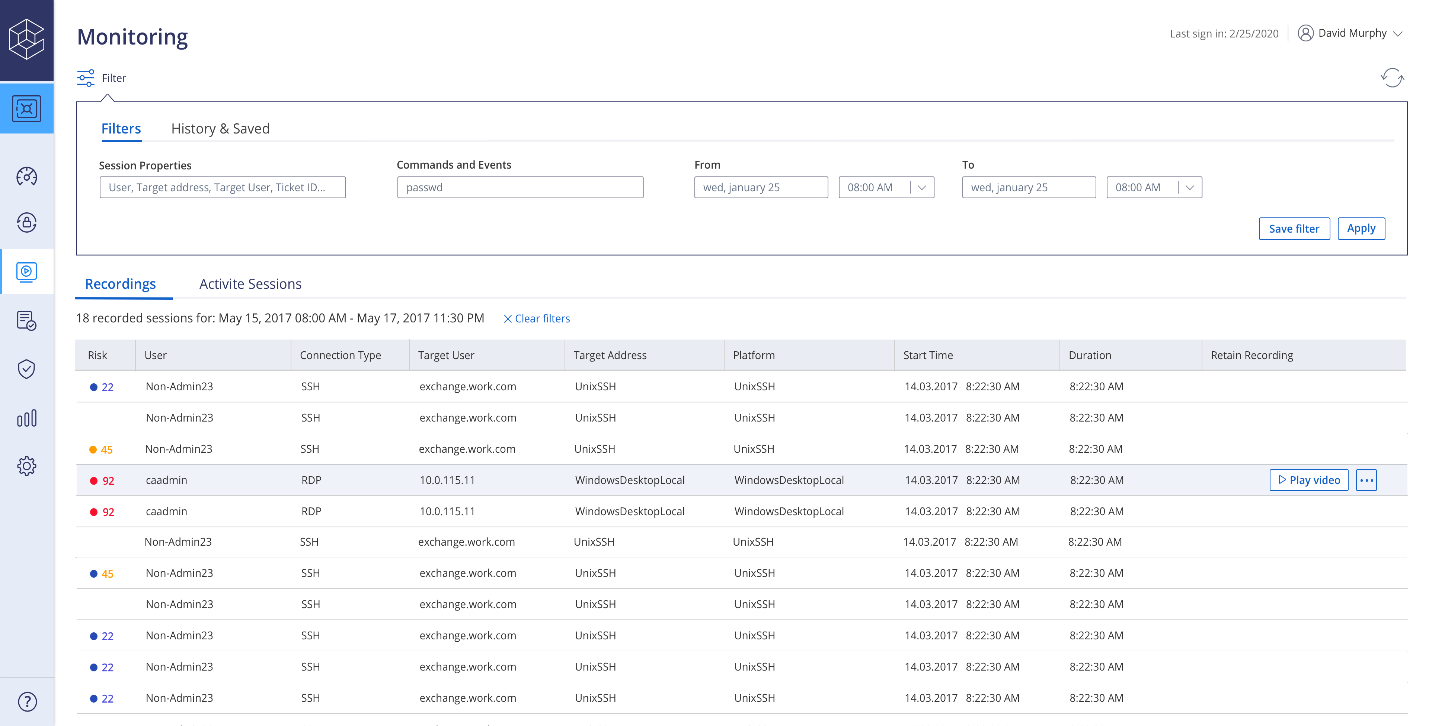
Take control of your organization’s security and minimize the risk of cyberattacks with Privileged Access Management (PAM) – the comprehensive solution to protect against internal and external threats.
Why This?
Condensed defense against internal and external threats
Enhanced operational performance
Lessen malware propagation and infection
Enables frictionless audit-friendly environment
To enhance security and simplify management, administrators can use the centralized policy management system to configure policies for password complexity, password rotation frequency, user access control and more. The system's automated password rotation feature strengthens security by eliminating the need for manual processes. It also automatically discovers and onboards privileged credentials and secrets used by both human and non-human identities.
Secure access to business resources is critical for protecting sensitive information. To achieve this, the tool implements context-aware Adaptive Multi-Factor Authentication and Single Sign-On to validate privileged users and ensure secure access.
Facilitates safe access to your Privileged Access Manager for both external vendors and remote employees, regardless of their location, without the need for VPNs, agents or passwords.
What You Gain?
Control access to privileged accounts.
Prevent privileged account attacks.
Regulate access in one location.
Restrain credential sharing.
Review risky behavior notifications in real-time
Integrate with identity and access management systems.



