As a seasoned professional in the field of technology, I’ve had the privilege of witnessing firsthand the evolution of security practices. One concept that has consistently stood out as a beacon of efficiency and effectiveness is Zero Standing Privileges (ZSP). Over the course of my career, I’ve become a staunch advocate for ZSP, recognizing its potential to revolutionize how organizations approach privilege management.
ZSP is a straightforward yet powerful principle that mandates that no user, regardless of their role or seniority, possesses inherent privileges. Instead, access is granted on a just-in-time basis, only when a specific task or action requires it. This approach eliminates the risks associated with excessive privileges, such as unauthorized access, data breaches, and insider threats.
In this blog, I have simplified
- What is Zero Standing Privileges
- Why use Zero Standing Privileges? A deeper dive
- Zero Standing Privileges More than Just In Time
- Embracing Zero Standing Privileges: A Proactive Approach
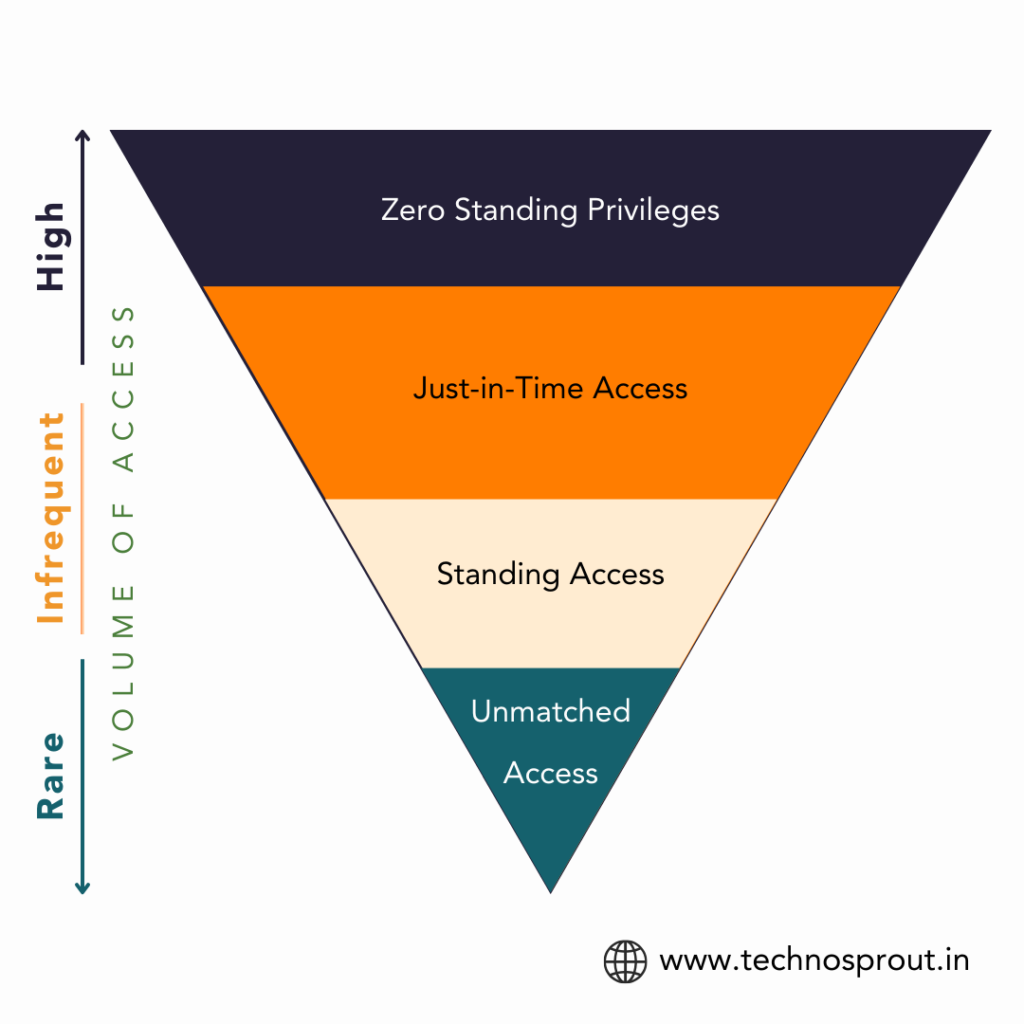
What is Zero Standing Privileges
From a security point of view, Zero Standing Privileges (ZSP) means that users don’t have permanent access to systems or data. They only get the necessary privileges when they need them, and these privileges are removed as soon as they’re no longer required.
Basically access will be provisioned (JIT) with ZSP meaning users have no standing privileges, meaning they are granted access only when explicitly requested and authorized.
Why Use Zero Standing Privileges? A Deeper Dive
ZSP offers a more granular approach to privilege management than traditional PAM methods. By focusing on permissions and entitlements rather than account ownership, it provides a more dynamic and adaptive security posture.
Here’s a breakdown of the key benefits of using ZSP:
1. Enhanced Security
- Reduced Attack Surface: By limiting persistent privileges, ZSP minimizes the potential for unauthorized access.
- Insider Threat Mitigation: It helps prevent insider threats by limiting employees’ access to only what they need to do their jobs.
- Data Breach Prevention: ZSP reduces the risk of data breaches by limiting the potential for sensitive information to be exfiltrated.
2. Improved Compliance
- Regulatory Adherence: ZSP aligns with many security regulations and standards, such as GDPR, PCI DSS, and HIPAA.
- Risk Reduction: By implementing ZSP, organizations can demonstrate a stronger commitment to security and compliance.
3. Increased Efficiency
- Automated Provisioning: ZSP can be automated to streamline the process of granting and revoking privileges.
- Reduced Administrative Burden: By reducing the number of privileged accounts, ZSP can lighten the administrative burden on security teams.
4. Greater Flexibility
- Dynamic Access: ZSP allows for more dynamic access control, enabling organizations to adapt to changing business needs.
- Context-Based Access: Privileges can be granted based on specific contexts, such as location, time of day, or device.
While ZSP may not be suitable for all scenarios, its benefits can be significant for organizations that prioritize security, compliance, and efficiency.
Zero Standing Privileges More than Just In Time
While ZSP and JIT share the fundamental principle of granting access only when necessary, ZSP offers a more comprehensive and granular approach.
Here’s how ZSP differs from JIT:
- TEA Controls: ZSP incorporates Time, Entitlement, and Approval-based controls to provide a more nuanced level of access management.
- Granular Control: TEA controls allow for more precise management of user sessions, ensuring that access is granted only for specific time periods and based on specific entitlements.
- Benchmarking: ZSP simplifies benchmarking by providing a clear framework for measuring the effectiveness of access controls.
- Robust Security: By combining JIT with TEA controls, ZSP offers a more robust and comprehensive approach to security.
In essence, ZSP is a superset of JIT, providing additional layers of security and control. By implementing ZSP, organizations can go beyond the basic principles of JIT to achieve a more secure and compliant environment.
ZSP-based controls are ideal for organizations seeking to:
- Enhance security: Reduce the risk of unauthorized access and data breaches.
- Streamline processes: Simplify user experience and improve efficiency.
- Expand PAM reach: Extend the benefits of privileged access management to a wider range of use cases.
- Facilitate adoption: Integrate seamlessly with existing workflows for easy user acceptance.
Embracing Zero Standing Privileges: A Proactive Approach
When considering ZSP, remember:
- Proactive Implementation: Don’t wait for a security breach to implement ZSP. Be proactive and explore options like JIT or vaulting if ZSP isn’t the best fit.
- Comprehensive Approach: ZSP is a valuable tool, but it’s not a one-size-fits-all solution. Consider a combination of controls like vaulting and JIT for maximum effectiveness.
- Future-Proofing: ZSP can help your organization stay ahead of evolving security threats and regulatory requirements.
By embracing ZSP, you’re taking a significant step towards enhancing your security posture and protecting your organization from potential risks.
A Confident Approach to Financial Identity Security with Technosprout
Embrace this holistic approach with Technosprout to identity security to ensure your financial operations can perform confidently. By strengthening your own company’s safety net, you protect not only your data and transactions but also the trust and confidence of your customers. Implement these strategies to stay agile and secure in a world where the stakes are as high as the rewards.
Amidst a myriad of MSSP options in the market, why opt for Technosprout? How can we help? What sets us apart?
Achieving cyber confidence begins with a solid strategy and governance. Technosprout leverages an “Assess, Design, Implement and Manage” four-pronged approach that leads organizations methodically through business transformation throughout the lifecycle
Our managed security services provide customized, comprehensive solutions, addressing specific business needs strategically along with the best certified experts and an experience of 7+ years in the market.
Don’t let your organization be the next target. Empower your organization and secure your Identities. We help implement and manage your Identity Security Game with CyberArk for complete risk mitigation. Strengthen your Identity with CyberArk Identity Access Management solutions and Technosprout Managed Services.






