Keeping sensitive data secure is a cornerstone of any cybersecurity strategy. However, the cloud throws a wrench into the idea of “least privilege” access. This blog post dives into the realities of data access governance (DAG) in today’s complex cloud environments and how a data-centric security approach can help you focus on protecting what truly matters: your valuable data.
Data Access Governance: Keeping Things Organized
Data access governance (DAG) is the process of setting up rules, procedures, and tools to manage how people and systems access your organization’s data. When done right, DAG ensures that only authorized users can view, change, and share sensitive information, following data security and compliance regulations.
The Cloud vs. Least Privilege: A Challenge
The principle of least privilege states that users and systems should only have access to the resources they absolutely need to do their jobs. In the context of data, this means giving people the minimum permissions required to see or modify data. For instance, an analyst studying customer purchases doesn’t need access to user email addresses if they can work with anonymized user IDs instead.
In the past, with data stored in on-premises warehouses, enforcing least privilege was easier. IT administrators tightly controlled these data platforms. Firewalls, VPNs, role-based access controls (RBAC), and user activity monitoring helped prevent unauthorized access.
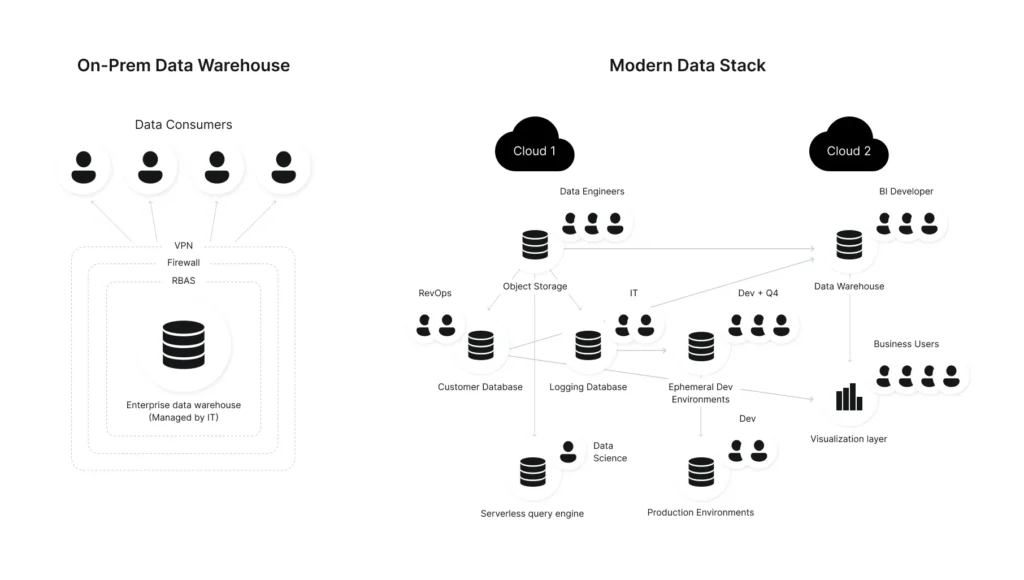
The cloud, however, changed the game. It made data more accessible to business teams, fostering a data-driven culture. But this also means more people and systems need access to data. While least privilege remains important, implementing it gets trickier when managing hundreds of users with various access needs.
The Decentralization Dilemma
Cloud infrastructure is easy to set up and manage by individual teams. But this decentralization makes it difficult to enforce consistent access control policies across the organization.
Multiple Access Points and Complexities
Cloud services can be accessed through various interfaces and APIs, often forming a tangled web of dependencies. Figuring out which permissions are truly necessary requires significant effort.
A Tower of Babel: IAM Across Vendors
Organizations using multiple cloud providers (CSPs) face the challenge of managing different IAM tools, each with its own user identities, authentication methods, and access policies. This makes it difficult to get a clear picture of overall user permissions.
Fragmented, API-Driven Architectures
The rise of data lakes and modern data stacks involves building a complex ecosystem of API-connected tools for data processing, storage, and analysis. Many of these tools may need access to sensitive data, adding another layer of permission management complexity.
Common Risks Associated with Weak Data Access Governance
- Lack of Accountability: Without proper oversight, unauthorized or excessive access can go unnoticed. Investigating security incidents becomes a challenge without clear audit trails of user activity and permissions.
- Example: A company discovers a customer data leak on the dark web. Due to intricate cross-account permissions, it takes weeks to pinpoint a compromised sales engineer account responsible for the breach, delaying efforts to identify other vulnerable resources.
- Example: A company discovers a customer data leak on the dark web. Due to intricate cross-account permissions, it takes weeks to pinpoint a compromised sales engineer account responsible for the breach, delaying efforts to identify other vulnerable resources.
- Compliance Violations: Regulations like GDPR and PCI DSS demand specific controls around data access. Having a clear view of who can access what data helps with evidence collection during audits.
- Example: A financial services firm subject to PCI DSS compliance experiences a violation due to mishandled permissions. A developer mistakenly copies sensitive payment card data to a non-compliant staging environment, which is discovered during an audit.
- Example: A financial services firm subject to PCI DSS compliance experiences a violation due to mishandled permissions. A developer mistakenly copies sensitive payment card data to a non-compliant staging environment, which is discovered during an audit.
- Data Exfiltration: Uncontrolled access to sensitive data significantly increases the risk of data loss, especially from insider threats or compromised credentials. This can lead to ransomware attacks or customer data breaches.
- Example: A contractor is granted temporary access to a customer database but their access isn’t revoked after the project ends. This goes unnoticed until months later, when the contractor downloads the database and sells it to a competitor.
Overcoming Cloud Data Access Challenges
You might be thinking, “Isn’t this just a permissions issue? Can’t IAM tools handle it?”
While IAM tools are crucial for managing user permissions and access controls, they’re complex and not specifically designed for data access challenges. They treat data storage like any other cloud resource, lacking awareness of the data itself and how it flows between services.
Cloud infrastructure entitlement management (CIEM) simplifies and streamlines IAM for cloud environments, reducing permission sprawl. However, not all CIEM tools are content-aware, meaning they may not identify who has access to sensitive data.
Data security posture management (DSPM) tools classify sensitive data, but not all offer DAG functionalities. Standalone DSPM tools can be limited without access awareness.
The key takeaway here is that data access challenges are not simply permission issues. Datastores have unique access patterns that often require broader and more dynamic access compared to other cloud resources. Additionally, not all data is created equal.
Take Control of Your Cloud Data
The cloud empowers your business, but it also introduces complexities around data access governance. Are you confident your sensitive data is truly secure?
This blog post highlighted the challenges of enforcing least privilege and maintaining control in a multi-cloud world. But fear not! There’s a better way.
Shift to a Data-Centric Security Approach
Technosprout, in partnership with cloud security leader Prisma Cloud, offers a powerful solution that puts your data first. Our comprehensive approach empowers you to:
- Gain complete visibility into your sensitive data across cloud environments.
- Enforce least privilege access and minimize the risk of unauthorized access.
- Simplify compliance by ensuring adherence to data security regulations.
- Reduce security risks with proactive threat detection and response.
Don’t wait for a data breach to act!
Contact Technosprout today to learn more about our data-centric security solutions and how we can help you achieve cyber confidence in the cloud.
Together, let’s ensure your data is secure and protected.





