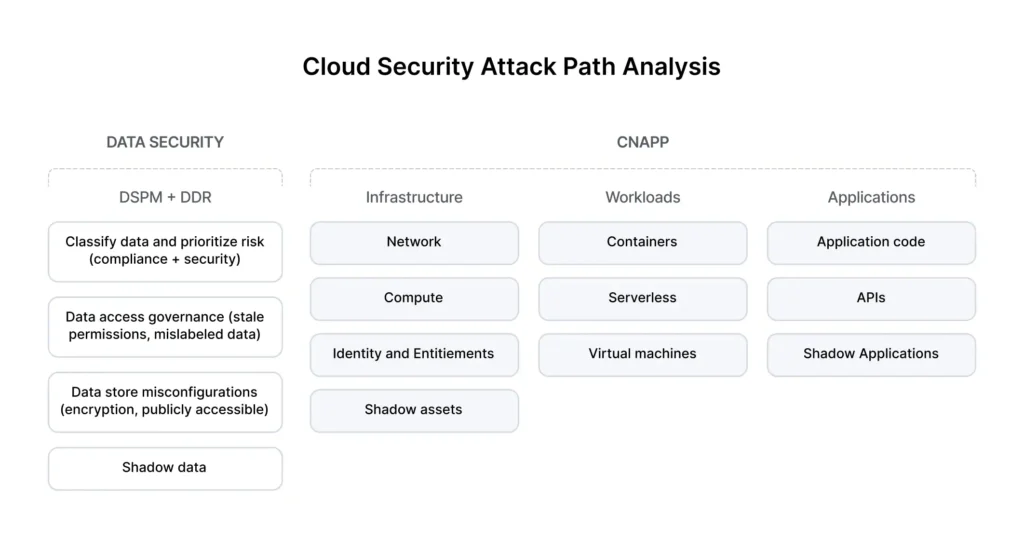
For cloud teams and security professionals, the ever-expanding attack surface in the cloud presents a significant challenge. Traditional security measures that focus solely on infrastructure configuration often leave critical blind spots, especially when it comes to data security. This is where Data-centric security comes in.
Imagine this scenario: you identify an unpatched virtual machine (VM) during a routine security scan. While an unpatched system is a cause for concern, from a purely technical perspective, it might not trigger an immediate red alert. But what if this VM houses a database brimming with sensitive customer information? Now the situation becomes infinitely more critical.
This is where data-centric security comes into play. By understanding the type of data you store in the cloud, its sensitivity level, and how it’s being accessed, you can prioritize vulnerabilities and respond to threats more effectively. This approach is particularly relevant in the cloud, where data is constantly on the move and traditional perimeter-based security models are no longer sufficient.
The Limitations of Configuration-Centric Security
Relying solely on configuration management tools has limitations. These tools excel at identifying misconfigurations and enforcing security policies at the infrastructure level. However, they lack the ability to:
- Identify and classify sensitive data: Configuration tools don’t inherently understand the context or value of your data.
- Prioritize vulnerabilities: A misconfigured VM is a security risk, but if it doesn’t store sensitive data, the remediation urgency might be lower compared to a compromised database containing customer credit card information.
- Detect suspicious data activity: Configuration tools can’t monitor data access patterns and identify anomalies that might indicate a potential data breach.
Shifting to Data-Centric Security Approach with DSPM
DSPM solutions address these limitations by providing a data-centric approach to cloud security. Here’s how DSPM empowers cloud and security teams:
- Data Discovery and Classification: DSPM tools employ automated discovery techniques to identify and classify sensitive data across your cloud environment. This includes data types such as personally identifiable information (PII), intellectual property, and financial data.
- Continuous Monitoring: DSPM offers real-time visibility into data access and activity. This enables teams to monitor for unusual data movement, unauthorized access attempts, or potential breaches.
- Risk Prioritization: By understanding the sensitivity of your data and the context in which it’s stored, DSPM helps prioritize vulnerabilities and remediation efforts. This allows you to focus on the issues that pose the greatest risk to your organization.
Data Detection and Response (DDR): Sealing the Gaps
While DSPM provides essential insights into your cloud data security posture, it’s crucial to have a mechanism for swiftly responding to security incidents. This is where Data Detection and Response (DDR) comes in.
DDR solutions work in tandem with DSPM to provide a comprehensive data security defense system. Here’s how DDR strengthens your security posture:
- Real-time Threat Detection: DDR leverages advanced analytics to detect anomalies and suspicious activity related to data access and movement.
- Automated Incident Response: DDR can automate incident response workflows, enabling teams to quickly isolate and contain threats before they escalate.
- Intelligent Threat Detection: DDR facilitates proactive threat detection by providing investigators with the data and context they need to identify and neutralize potential threats.
The Power of DSPM and DDR: A Winning Combination
By combining DSPM and DDR, cloud and security teams gain a powerful duo for safeguarding sensitive data in the cloud. DSPM sheds light on your data landscape, while DDR equips you with the solutions to swiftly respond to threats.
This holistic approach empowers you to:
- Strengthen your security posture: Proactive identification and classification of sensitive data coupled with real-time monitoring minimizes the attack surface.
- Minimize data breaches: Early detection and response to suspicious activity enable you to contain threats before they result in a data breach.
- Ensure compliance: DSPM and DDR can help you meet regulatory compliance requirements for data security.
Don’t leave your data security in the shadows. See how DSPM + DDR can illuminate your cloud environment and empower your teams to proactively safeguard sensitive data.





