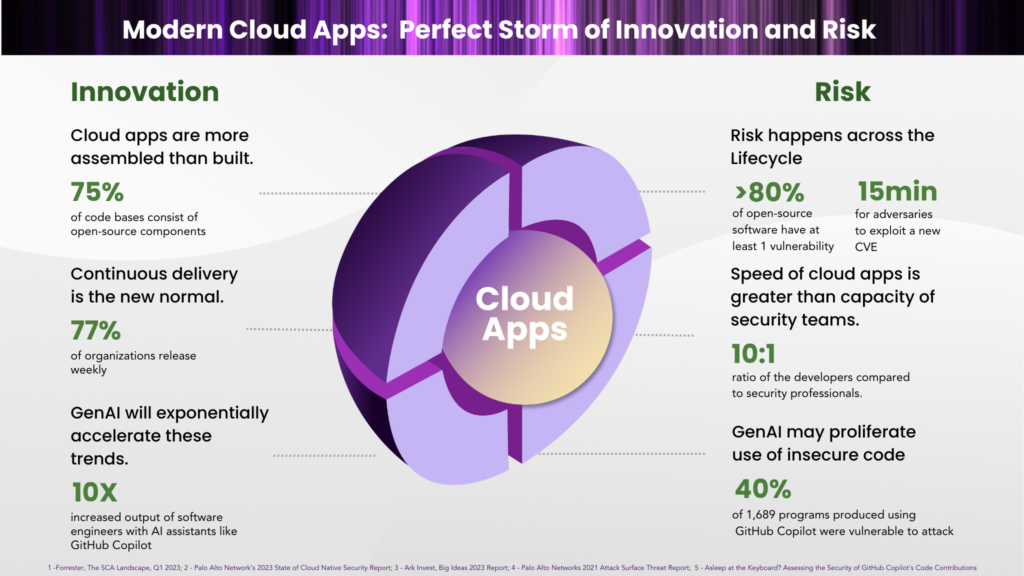
Banking services companies are in a constant state of flux. From Private banks to public banks, all face a multi-pronged challenge when it comes to their digital offerings and security.
Customers demand a frictionless, secure, and agile experience. Meanwhile, C-suite executives and product leaders push for breakneck speed to market. They demand high-quality, innovative products that differentiate their offerings in a crowded marketplace. Adding another layer of complexity, regulators keep a watchful eye, enforcing strict compliance requirements and demanding robust security controls.
The consequence? A development process fraught with tension. Development teams feel like they’re constantly under siege, juggling competing priorities and facing a barrage of last-minute changes. Security teams, often seen as roadblocks rather than collaborators, struggle to implement effective controls without hindering progress. This lack of transparency and siloed approach leaves everyone in the dark, creating a breeding ground for errors and vulnerabilities.
The solution for this risk prevention is to Shift Left and enable DevSecOps
In this blog let’s explore
- What does it mean to Shift Left?
- Benefits of Shift Left
- Benefits of a Secure Build Phase
- Benefits of Secure Deployment
- Benefits of Comprehensive Runtime Protection
- Shift Left with Technosprout Managed Services and Empower Your Cloud Strategy
What does it mean to Shift Left?
“Shift Left” isn’t new. It’s a DevOps philosophy that emphasizes integrating security testing for quality and performance earlier in the development process. Think “test early, test often,” as Microsoft famously phrased it.
The goal? Faster releases with mitigated risks and security vulnerabilities. Addressing issues early avoids costly fixes later and ensures predictable, high-quality software that meets brand promises, customer needs, and regulations.
The “Shift Left” approach to software development can bridge the gap between competing demands in financial services. This strategy emphasizes integrating security and quality checks earlier in the Software Development Lifecycle (SDLC).
Traditional, late-stage security checks can be disruptive when audits uncover issues. Shift Left empowers financial institutions to:
- Proactively address security concerns: Early detection minimizes last-minute fixes required to meet compliance deadlines.
- Streamline development: Integrating security into the process reduces delays and rework, accelerating deployments.
By prioritizing security upfront, “Shift Left” fosters a culture of collaboration, allowing development, security, and regulatory teams to work together for a common goal: secure, compliant, and timely application releases. In a nutshell, Shift left and secure applications by design from Code to Cloud.
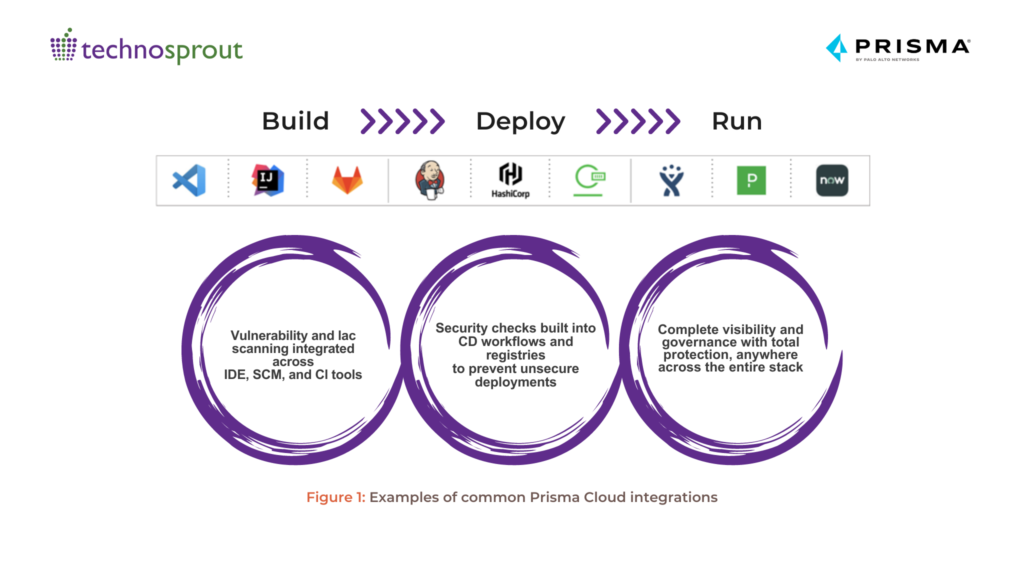
Benefits of Shift Left
- Comprehensive Scanning: Identify and address vulnerabilities and misconfigurations early. Prisma Cloud scans virtual machine images, container images, Pivotal Application Service (PAS) droplets, serverless functions, and even your infrastructure-as-code (IaC) templates used with Terraform, CloudFormation, Kubernetes manifests, and similar technologies.
- Frictionless Integration: Leverage existing tools within your development workflow. Prisma Cloud integrates seamlessly with IDEs, source code management (SCM), and CI/CD pipelines for a smooth experience.
- Enforced Security Gates: Security teams take control. Define quality gates within the pipeline. If Prisma Cloud detects vulnerabilities or compliance issues, it can halt the build, forcing developers to address the problems before the software progresses any further. This proactive approach prevents insecure code from reaching production.
Benefits of a Secure Build Phase:
- Empowered Developers: Early detection and remediation minimize rework, allowing developers to focus on innovation.
- Faster & More Secure Deployments: A secure build phase streamlines deployments and reduces the risk of security breaches in production environments.
- Reduced Risk & Enhanced Compliance: Proactive security strengthens your overall security posture and simplifies compliance with regulations.
Even the most secure build can be compromised by newly discovered vulnerabilities. Prisma Cloud goes beyond the build phase to provide continuous vigilance throughout the deployment process:
- Post-Build Security Scans: Prisma Cloud scans container registries and serverless repositories to identify any vulnerabilities discovered after the build. This ensures even the latest threats are addressed before deployment.
- Enforcing Trusted Code Sources: Only deploy code you can trust. Prisma Cloud enforces the use of pre-approved sources for container images and serverless functions, minimizing the risk of introducing vulnerabilities.
- Deployment Security Gates: Security doesn’t stop at the build phase. Prisma Cloud acts as a final security checkpoint during deployment. If your defined security requirements aren’t met, the deployment is halted, preventing potentially risky code from reaching production.
Benefits of Secure Deployment:
- Continuous Security: Prisma Cloud’s multi-layered approach ensures ongoing security throughout the development lifecycle.
- Reduced Risk: By identifying and addressing vulnerabilities before deployment, you significantly reduce the attack surface for malicious actors.
- Confidence in Every Release: Deployment security gates provide peace of mind, knowing only code meeting your strict security standards reaches production.
Even with robust deployment security, runtime threats can emerge. Prisma Cloud offers a comprehensive solution that goes beyond stopping insecure code:
- Context-Aware Risk Prioritization: Not all vulnerabilities are created equal. Prisma Cloud automatically ranks every issue based on its severity and how it impacts your specific environment and usage patterns. This helps security teams prioritize critical issues and focus on the areas with the biggest impact.
- Direct Developer Notification: Improve developer accountability and streamline remediation. Leveraging application metadata and tags captured during the CI stage, Prisma Cloud directly notifies the responsible developer within their existing development tools. This eliminates finger-pointing and accelerates the remediation process.
- Continuous Runtime Protection: Prisma Cloud provides real-time security for your running applications and cloud infrastructure. It continuously monitors for anomalies, malware, and zero-day attacks, ensuring your environment remains secure.
Benefits of Comprehensive Runtime Protection:
- Faster Remediation: Targeted notifications and risk prioritization enable security teams to focus on the most critical issues first.
- Improved Developer Productivity: Direct communication within familiar tools empowers developers to quickly fix their code.
- Reduced Attack Surface: Continuous monitoring minimizes the window of vulnerability and helps prevent breaches.
- Streamlined DevSecOps: By streamlining communication and remediation, Prisma Cloud bridges the gap between development and security, fostering a collaborative DevSecOps environment.
The key takeaway? Prioritization is key. When everything is deemed a top priority, nothing truly gets the focus it deserves. Engineering and security teams need to collaborate to identify the true “red lines” that must be non-negotiable.
By striking a balance between essential controls and operational flexibility, banks can achieve a more secure and adaptable security posture.
Shift Left with Technosprout Managed Services and Empower Your Cloud Strategy
Prevent risks by securing infrastructure and applications by design. Technosprout along with its trusted partner Prisma Cloud enables you to shift left and integrate security into developer tools and workflows so that you can keep pace with the agility and rapid release cycles.
Achieving cyber confidence begins with a solid strategy and governance. Technosprout leverages an “Assess, Design, Implement and Manage”four-pronged approach that leads organizations methodically through business transformation throughout the lifecycle.
Our managed security services provide customized, comprehensive solutions, addressing specific business needs strategically along with the best certified experts and an experience of 7+ years in the market.
Don’t let your organization be the next target. Empower your organization and secure your data. We help implement a Multi-Cloud Security Strategy, helping you protect your Application, Access, and Data.





